Cyber-security
2023 JUN 21
Mains >
Security > Cyber Security > Cyber warfare
WHY IN NEWS?
- On June 12, reports emerged that a bot on the messaging platform Telegram was allegedly returning personal data of Indian citizens who registered with the COVID-19 vaccine intelligence network (CoWIN) portal for vaccination purposes. The bot spewed out personal details like name, Aadhaar and passport numbers upon entry of phone numbers.
- This is not the first time reports about data leaks have emerged. In January 2022, the personal data of thousands of people in India were reportedly leaked from a government server. The information included COVID-19 test results, phone numbers, names and addresses of citizens. The data could be accessed via online search. In December, in a separate security breach, an Iranian hacker claimed to be in possession of data from the CoWIN database.
WHAT IS CYBER SECURITY?
- Cyber security involves the techniques of protecting computers, networks, programs and data from unauthorized access or attacks that are aimed for exploitation.
- The concept includes guidelines, policies, safeguards, technologies, tools and training to provide the best protection for the cyber environment and its users.
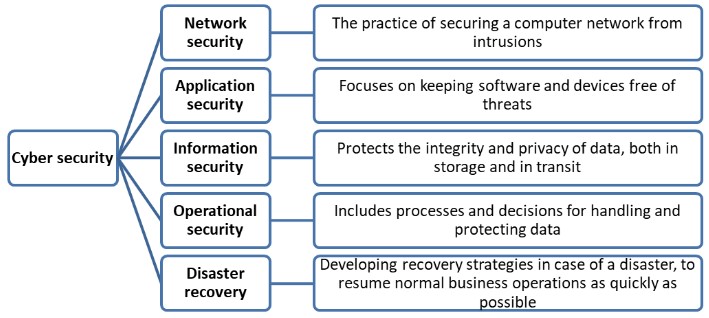
TYPES OF CYBER ATTACKS:
- Cyber-attack can be defined as any act that compromises the security expectations of an individual, organization, or nation in its cyber space.
- Based on perpetrators and their motives, Cyber threats can be categorized into:
- Cyber Espionage:
- Refers to the use of computer networks to gain illicit access to confidential information, typically that held by a government or other organization.
- The 2019 cyber-attack on Kudankulam nuclear power plant using a data extraction malware falls under this category.
- Cyber Crime:
- Cybercrime is any criminal activity that involves a computer, networked device or a network.
- Most cybercrimes are carried out in order to generate profit for the cybercriminals.
- However, some cybercrimes are carried out against computers or devices directly to damage or disable them, to spread malware, illegal information, images or other materials. Some cybercrimes do both.
- Cyber Terrorism:
- It is the convergence of terrorism and cyber space.
- It refers to unlawful attacks and threats of attacks against computers, networks and information stored to intimidate or coerce a government or its people in furtherance of political or social objectives.
- They are offensive maneuvers that targets computer information systems, infrastructures or computer networks, with an intention to damage or destroy targeted computer network or system.
- Cyber Warfare:
- Though there is no proper definition, it may be defined as actions by a nation-state or its proxies to penetrate another nation’s computers or networks for the purposes of espionage, causing damage or disruption.
- It is perceived to be the fifth domain of warfare.
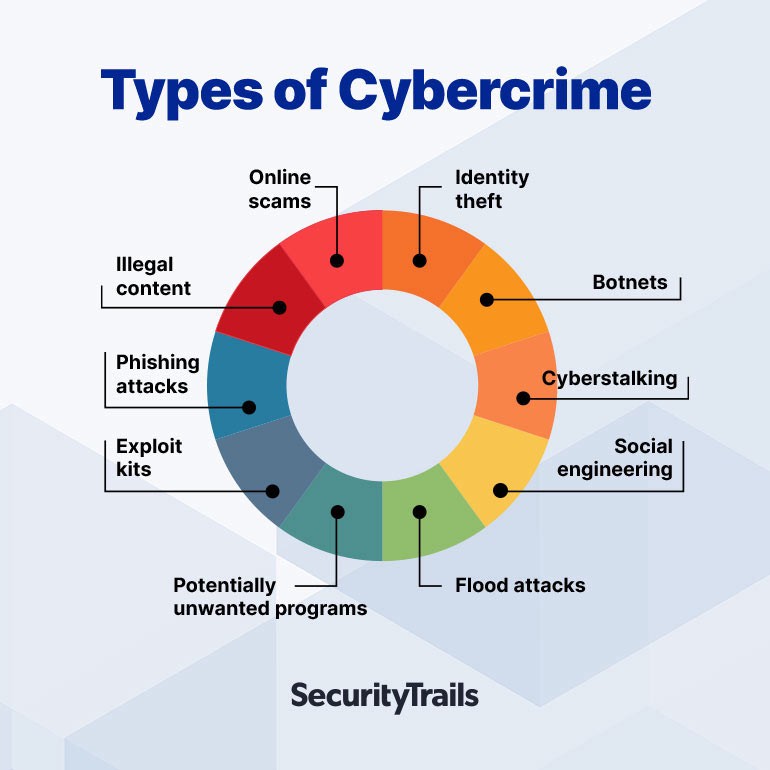
TYPES OF CYBER-CRIMES:
STATISTICS:
- According to 'Crime in India’, released by the National Crime Records Bureau 2021:
- Cybercrimes recorded an increase of 11.8% in 2020
- Cybercrimes have increased four times or 306 percent in the past four years and rate of cybercrime (incidents per lakh population) increased in 2020.
- Number of cases registered under Cyber Crime against Children during 2019 was 305.
- As per data by CERT-In
- 1.16 million cases of cyberattacks were reported in 2020, up nearly three times from 2019 and more than 20 times compared to 2016.
- Over 26,100 Indian websites were hacked during 2020
- As per Norton Cyber Safety report 2021:
- 59% of adults in India have become victim of cyber crime
- As per ‘Cyberthreats to Financial Organizations in 2022’ report:
- India is among the top five targets for cyberattacks in the Asia Pacific (APAC) region, particularly security breaches that involve cyber espionage.
- As per State of Ransomware 2021
- 68% of organizations in India deals with ransomware
- Global Cyber Security Index of ITU 2020
- India scored 97.5 points to make it to the 10th position worldwide in the GCI 2020. This was an improvement from 47th rank in 2019.
RECENT EXAMPLES OF MAJOR CYBER-ATTACKS IN INDIA:
- Attack on Air India (2021):
- India's national airline suffered a cyber-attack on its data servers, which affected about 4.5 million customers around the world.
- Details including passport and ticket information as well as credit-card data were compromised.
- Data breach on Domino’s India (2021):
- Jubilant FoodWorks, which owns Domino's India, experienced a security incident where data of 18 crore orders of Domino's India became public.
- Malware attack at Kudankulam Nuclear Power Plant (2019):
- A malware infection was detected on the administrative network used for day-to-day administrative activities.
- Aadhaar data leak (2019):
- As recently as February 2019, Aadhaar details of over 6.7 Million users containing details such as names, addresses and the numbers were leaked.
- Cyber Attack on Cosmos Bank (2018):
- A cyber-attack on Cosmos Bank’s Pune branch saw nearly 94 crores rupees being siphoned off by hackers to a Hong Kong situated bank.
- WannaCry & Petya ransomware attacks (2017):
- The ransomware attacks made its impact felt across the world, including India, where several thousand computers got locked down by ransom-seeking hackers.
- The attack also impacted systems belonging to the Andhra Pradesh police and state utilities of West Bengal and certain functions at Jawaharlal Nehru Port Trust.
- Data thefts at Zomato (2017):
- The food tech company discovered that data, including names, email IDs and hashed passwords, of 17 million users was stolen by a hacker.
- Scorpene submarine data leak (2016):
- Combat and performance capabilities of six Scorpene-class submarines produced by India in partnership with French company DCNS have been leaked in 2016.
SIGNIFICANCE OF CYBER SECURITY:
- Increasing internet use in India
- With over 600 million internet users, India is the second largest online market in the world, ranked only behind China.
- It was estimated that by 2023, there would be over 650 million internet users the country.
- This demands increased focus security in internet spaces
- Increasing digitisation in India
- Digital India initiatives, Land records digitization, Digital Health Mission, Aadhar, Increasing cashless economy etc. puts further pressure on the need for a secure cyber architecture in the country.
- Constitutional obligations:
- After K.S. Puttaswamy verdict of Supreme Court, the state is obliged to secure right to privacy of its citizens >> for which cyber security is an essential component.
- Economic value of data is increasing with emerging techs:
- Increased penetration of big data analytics, AI, social media level marketing etc. makes data more valuable >> hence cyber-space where huge amount of data is generated becomes more vulnerable and susceptible to security threats.
- Increased instances of cyber-crimes:
- Cyber-crimes are on rise at global and national level
- Few famous examples:
- Wannacry ransom ware, Stuxnet attack on Iran, Leak of scorpene class submarine
- As per Data Security Council of India report India is second most cyber-attack affected country between 2016-18
- Critical Infrastructure:
- Safety and security of critical infrastructure such as Aadhar, NATGRID, Health Stack, Nuclear plants etc. are heavily depend upon secure cyber architecture.
- Cost incurred due to cyber-attacks are increasing:
- Cost to the world in 2021 from cyber attacks likely to range between USD 3trillion - 4 trillion.
- India has lost a huge amount of money each year in cyber-attacks. For instance, cybercrimes in India caused losses of Rs. 1.25 lakh crore in 2019.
MEASURES TAKEN TO IMPROVE CYBER SECURITY:
- Institutions:
- National Critical Information Infrastructure Protection Centre:
- It is created under IT Act, 2000
- It is mandated to facilitate the protection of critical information infrastructure.
- National Cyber Security Coordinator:
- He/she advises the Prime Minister on strategic cybersecurity issues.
- Computer Emergency Response Team (CERT-In):
- Which is the nodal entity responding to various cybersecurity threats to non-critical infrastructure comes under the Ministry of Electronics and Information Technology (MEITY).
- Defence Cyber Agency:
- Under Ministry of Defence
- A tri-service command of the Indian armed forces to coordinate and control joint cyber operations, and craft India’s cyber doctrine
- Indian Cyber Crime Coordination Centre (I4C):
- It was rolled out by Ministry of Home Affairs for the period 2018-2020 to combat cybercrime in the country, in a coordinated and effective manner
- Cyber Swachhta Kendra (Botnet Cleaning and Malware Analysis Centre):
- It has been launched for detection of malicious programs and provides free tools to remove the same.
- National Technical Research Organization
- The agency specializes in multipile disciplines, which include remote sensing, data gathering and processing, cyber security, geospatial information gathering, cryptology, strategic hardware and software development.
- Policies:
- National Cyber Security Strategy 2020:
- Formulated by the Office of National Cyber Security Coordinator at the National Security Council Secretariat.
- Objectives:
- Improve cyber awareness and cyber-security through more stringent audits. Empanelled cyber auditors will look more carefully at the security features of organisations than are legally necessary now.
- To ensure table-top cyber crisis management exercises regularly to reinforce the idea that cyber-attacks can take place regularly.
- Call for an index of cyber preparedness, and attendant monitoring of performance.
- Call for a separate budget for cybersecurity
- To synergise the role and functions of various agencies with the requisite domain knowledge.
- National Cyber Security Policy 2013
- Creation of Secure Cyber Ecosystem:
- To create a secure cyber ecosystem in the country, generate adequate trust & confidence in IT systems and transactions in cyberspace and thereby enhance adoption of IT in all sectors of the economy.
- Compliance to Global Security Standards:
- To create an assurance framework for design of security policies and for promotion and enabling actions for compliance to global security standards and best practices by way of conformity assessment (product, process, technology & people).
- Strengthening the Regulatory Framework:
- To strengthen the Regulatory framework for ensuring a Secure Cyberspace ecosystem.
- NCIIPC:
- To enhance the protection and resilience of Nation’s critical information infrastructure by operating a 24×7 National Critical Information Infrastructure Protection Centre (NCIIPC) and mandating security practices related to the design, acquisition, development, use and operation of information resources.
- Indigenization of Technologies:
- To develop suitable indigenous security technologies through frontier technology research, solution oriented research, proof of concept, etc.
- Testing and Validation:
- To improve visibility of the integrity of ICT products and services by establishing infrastructure for testing & validation of security of such products.
- Human Capacity Development:
- To create a workforce of 500,000 professionals skilled in cyber security in the next 5 years through capacity building, skill development and training.
- Safeguarding Privacy:
- To enable protection of information while in process, handling, storage & transit so as to safeguard privacy of citizen’s data and for reducing economic losses due to cybercrime or data theft.
- Tackling cybercrime:
- To enable effective prevention, investigation and prosecution of cybercrime and enhancement of law enforcement capabilities through appropriate legislative intervention.
- Surveillance:
- Central Monitoring System Project:
- Government has set up the CMS to automate the process of lawful interception and monitoring of mobile phones, landlines and the internet in the country.
- The project is run by Centre for Development of Telematics.
- Network Traffic Analysis (NETRA):
- It has been developed by the CAIR laboratory under the DRDO
- The system could detect selective words like “bomb”, “blast”, “attack” or “kill” within seconds from emails, instant messages, status updates and tweets.
- National Intelligence Grid (NATGRID):
- NATGRID was proposed just after the 26/11 Mumbai attacks.
- It is an intelligence grid that links all the stored data from different government and intelligence entities, which enables it to analyse data gathered by the linked agencies.
- Lawful Interception and Monitoring Project (LIM):
- The LIM works in a similar way to NETRA.
- It is a program for surveillance of Internet traffic in India, allowing the monitoring of all traffic (text and audio) passing through ISPs >> without the ISP’s knowledge.
- Reporting:
- National Cyber Crime Reporting Portal:
- It caters to complaints pertaining to cybercrimes only with special focus on cybercrimes against women and children
- Legal Framework:
- Information Technology Act, 2000
- It was enacted to give legal sanction to electronic commerce and electronic transactions, to enable e-governance, and also to prevent cybercrime.
- The law prescribes penalties for various cybercrimes and fraud through digital/electronic format.
- It also gives legal recognition to digital signatures.
- It provides for the establishment of a Cyber Regulatory Appellant Tribunal under the Act. This tribunal will handle all appeals made against the order of the Controller or Adjudicating Officer.
- Indian Telegraph Act, 1885
- It gives the Government of India exclusive jurisdiction and privileges for establishing, maintaining, operating, licensing and oversight of all forms of wired and wireless communications within Indian territory.
- It also authorizes government law enforcement agencies to monitor/intercept communications and tap phone lines under conditions defined within the Indian Constitution.
- Section 5(2) of the act allows central and state governments to prevent the transmission of messaging during a “public emergency or in the interest of public safety”, or “in the interests of the sovereignty and integrity of India, the security of the state”.
- Personal Data Protection Bill
- The Bill seeks to provide for protection of personal data of individuals, and establishes a Data Protection Authority for the same.
- National e-governance plan:
- It takes a holistic view of e-Governance initiatives across the country, integrating them into a collective vision, a shared cause.
- Cyber Crime Volunteers Programme (lateral surveillance):
- Launched by Indian Cyber Crime Coordination Centre, under the Ministry of Home Affairs through cybercrime grievance portal
- To allow citizens to register themselves as “Cyber Crime Volunteers’’ in the role of “Unlawful Content Flaggers”.
- It is rolled out as a part of cyber hygiene promotion to bring together citizens to contribute in the fight against cybercrime
- Transition in the outlook from a ‘punishing state’ to a ‘preventive state’.
- State initiatives : C-Plan App in Uttar Pradesh
- Preventive efforts:
- National Security Directive on the telecommunication sector:
- The objective was to specifically check for any ‘backdoor’ or ‘trapdoor’ vulnerabilities in the telecom networks
- Government barred BSNL and MTNL from using Chinese equipment for the roll-out of its 4G network.
- Private sector collaboration:
- Cyber Surakshit Bharat initiative:
- It was launched in 2018 by the MeitY.
- It is the first public-private partnership of its kind that leverages the expertise of the IT industry in cyber security along with MeitY’s organizations such as CDAC, CERT-In, NIC, and STQC as the knowledge partners in this training program.
- Microsoft is a founding partner of the Cyber Surakshit Bharat initiative
- Cyber-security skills development campaign:
- Microsoft has introduced a cybersecurity skills development campaign in 23 geographies, including India, to address the alarming shortage of internet security professionals.
- By 2025 there will be 3.5 million cybersecurity jobs available globally, representing a 350% increase over an eight-year period.
- By that time, India alone is estimated to have almost 3.5 lakh cybersecurity job positions waiting to be filled, both in the private and public sectors.
- Cyber Shikshaa:
- For training underprivileged young women in cybersecurity
- Global cooperation:
- Convention on Cybercrime (Budapest Convention):
- It is the first international treaty seeking to address Internet and computer crime (cybercrime) by harmonizing national laws, improving investigative techniques, and increasing cooperation among nations.
- It was drawn up by the Council of Europe with the active participation of the Council of Europe's observer states Canada, Japan, Philippines, South Africa and the United States.
- India is not a party
- 'Paris Call for Trust and Security in Cyberspace’
- For stability and security in the information space
- The International Telecommunication Union (ITU):
- It is a specialized agency within the UN which plays a leading role in the standardization and development of telecommunications and cyber security issues.
- Christchurch Call to Action (NZ):
- 52 countries and international bodies have signed the Christchurch Call to Action to eliminate terrorist and violent extremist content online.
- Global Centre for Cybersecurity:
- It was launched by the World Economic Forum (WEF) to serve as laboratory and early-warning think tank for future cyber security scenarios and help build a secure global cyberspace.
- Internet Governance Forum (IGF):
- It brings together all stakeholders i.e. government, private sector and civil society on the Internet governance debate.
- Internet Corporation for Assigned Names and Numbers (ICANN):
- It is a non-profit organization responsible for coordinating the maintenance and procedures of several databases related to the namespaces and numerical spaces of the Internet, ensuring the network's stable and secure operation.
CONCERNS:
- Lack of awareness:
- Almost 80% of cybercrime frauds occur due to lack of cyber knowledge.
- Exponential growth of digital space due to pandemic:
- The pandemic has resulted in digital technology adoption being fast forwarded and the demand for technology-driven products increasing multifold.
- But this growth has further exposed our cyber vulnerabilities
- During Covid-19 pandemic, overuse or addiction to social media and increased use of online mode to earn money led to rise in cybercrimes.
- Weak digital security:
- Out-dated infrastructure with poor or inadequate cyber security protection has exposed India’s digital vulnerability.
- Examples:
- Aadhaar data leakage.
- Leak of data about scorpene class submarine
- Issues with India's cyber security institutions:
- Multiple organizations and overlapping responsibilities - India has 36 different central bodies that deal with cyber issues
- Lack of clear institutional boundaries and accountability.
- Limited inter-agency coordination:
- Cyber-crimes often pans across the jurisdiction of different agencies, such as state police forces, Enforcement Directorate, departments under Home and Foreign Affairs Ministries etc.
- However, till recently there has been no proper mechanism to ensure the smooth coordination between these agencies in matters of data sharing, investigation etc.
- Lack of collaboration between and public and private players:
- Private sector, despite being a major stakeholder in the cyberspace, has not been involved proactively for the security of the same.
- India is yet to clearly articulate a doctrine that holistically captures its approach to cyber conflict:
- The absence of a credible cyber deterrence strategy means that states and non-state actors alike remain incentivised to undertake low-scale cyber operations
- Service hub:
- India is home to a large share of IT and service-sector industries.
- It hosts some of the largest outsourcing services in the world.
- To add to this, through several initiatives such as Digital India, the government is pushing for large scale digitization. This not only attracts tech investors, but also tech criminals.
- Increased penetration of crypto-currencies:
- Cryptocurrency, in particular Bitcoin, will fuel the rise and evolution of the ransomware industry
- Lack of resources:
- Lack of manpower, training and indigenization in hardware and software cyber security tools is pushing it to a more vulnerable position.
- For instance, like Israel’s National Cyber Directorate or US’s Cyber security and Infrastructure Security Agency Act (CISA), India doesn’t have any active mechanism for cyber defence.
- Shortage of professionals:
- Despite having high demand for cybersecurity professional, India is facing an acute talent shortage in this sector.
- It has been estimated that as of 2020-end, India faced a shortage of 1.5 million cyber security professionals.
- Anonymity:
- Law enforcement is handicapped by the fact that cybercriminals can operate from anywhere with internet access.
- Regulatory mechanism not equipped:
- IT Act, 2000, is not equipped to consider new-age changes in the mode of functioning of businesses and modus operandi of crimes in cyber space.
- Tussle between regulator and social media intermediaries
- Example: Tussle between Govt and micro blogging site Twitter
- Intermediaries commitment towards customers:
- Tech companies that use end-to-end encryption argued that they could not open a backdoor for identifying originators >> it would be a breach of promise to their subscribers.
- External attacks:
- Examples:
- Shadow Network:
- It is a China-based computer espionage operation that stole classified documents and emails from the Indian government, the office of the Dalai Lama, and other high-level government networks
- Suckfly:
- It is a China-based threat group, known to have conducted cyber-attacks on several Indian government and commercial organisations recently.
- Dtrack:
- Targeted Indian banks and Kudankulam nuclear power plant in 2019.
- Spying through commercial establishments:
- Chinese vendors Huawei and ZTE have been under global scrutiny for allegedly installing backdoor vulnerabilities and spying for the Chinese government and have been banned by several countries.
- UMBRAGE project:
- As per documents released by WikiLeaks, Central Intelligence Agency's (United States) UMBRAGE project have advanced capabilities of misdirecting attribution to another nation-state (“false flag attacks”) by leaving behind false “fingerprints” for investigators to find.
- Obsolete systems:
- India is a major destination for cheap electronic imports with inadequate security features.
- Also, there is rampant use of unlicensed software and cracked licenses. These factors make the country susceptible to hacking and other malware attacks.
- Offshore servers:
- Most service providers in India use data servers and processing centers located beyond the geographical boundary of India.
- This has proved to be a major hindrance in investigating cybercrimes and ensuring that the firms abide by the Indian cyber and privacy laws.
- Under reporting:
- As per National Crime Records Bureau, Cybercrimes accounted for less than a percentage (0.43%) or 21,796 cases of a total of 50,07,044 cognizable crimes in 2017.
- This indicates a severe case of under reporting of cybercrimes.
- A major reason for the same among individuals is the lack of awareness regarding cybersecurity. In case of organisations and Service sector industries, it is the fear of loss of reputation.
- Jurisdictional Uncertainty:
- Cybercrimes cut across territorial borders which undermine the feasibility and legitimacy of applying domestic laws.
- In the absence of a single internationally recognized code of law and procedure governing cybercrimes the law enforcing authorities of individual countries find it extremely difficult to tackle cybercrimes and criminals while applying their territorial law.
- Reliance on Chinese equipment in telecom sector:
- For instance: 30% of Bharti Airtel’s network comprises Chinese telecom equipment and it is 40% for Vodafone Idea’s network.
WAY FORWARD:
- We need a ‘cyber-security doctrine’ similar to our Nuclear doctrine:
- A clear public posture on cyber defence and warfare >> enable a more stable and secure cyber ecosystem.
- It will also boosts citizen confidence, helps build trust among allies, clearly signals intent to potential adversaries and ensures greater transparency
- It will be also useful in conducting offensive cyber operations
- Establish National Cyber Security Commission (NCSC):
- To coordinate with all ministries for National Critical Information Infrastructure (NCII) in their areas and play a catalytic role for the requirements of military in cyber warfare.
- Human resource development:
- By 2025, the cybersecurity space is expected to generate around a million jobs in India.
- For it to be beneficial for India’s demographic dividend, India must invest in capacity building and skill development.
- Thrust on digital education:
- A critical component of cyber-security is education
- Digital literacy must be made part and parcel of school curriculums.
- People must be made aware of the relevance of cyber security.
- For the same, the scope of initiatives under Digital India campaign needs to be enlarged.
- Technology industry, civil society and the government should coordinate to make users aware of cyber threat vectors such as phishing, viruses, and malware.
- ‘Atmanirbhar’ in cyber systems:
- Indigenous capability in manufacture of electronics should be boosted, so as to reduce India’s import dependency.
- The government should also strengthen its monitoring of electronics import, so that only reliable products make their way to the Indian markets.
- Improved coordination
- Improved coordination is needed between the government and the private sector, as well as within the government itself —and at the national and State levels.
- Cooperation between technology service companies and law enforcement agencies>>> vital part of fighting cyber crime
- Role of Internet intermediaries:
- Intermediaries should deploy automated tools for proactively removing or disabling public access to unlawful information
- Intermediaries should have a 24x7 mechanism to deal with requisitions of law enforcement.
- Capacity building:
- Self-attack to find vulnerabilities to fix them- to build cyber-security resilience
- Establishment of security firewalls - as first line of defence to fend off threats from external systems.
- Map hotspots area:
- States should map the cybercrime hotspots (ex: Jamtara of Jharkhand) which will help in quick detection and take proactive measures to prevent cybercrimes.
- Proper investigations:
- Development and continual upgradation of cyber forensics capabilities and investigating skills of enforcement agencies, to handle cyber-crimes in the ever-expanding proliferation of devices, platforms, big data, Internet of Things, mobility and social media.
- Zero-trust approach:
- Zero trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network.
- Organizations need to adopt a zero-trust approach to their security strategy.
- Promote cutting edge technologies:
- Research should be encouraged to leverage artificial intelligence (AI) to monitor, detect and verify the legitimacy of threats and automate response to the threats.
- Encourage investment in cybersecurity:
- The private must be persuaded to actively invest in cyber security.
- At present, only a part of security budget is being utilized for IT security by companies.
- The government should also play its role, by creating degree and PG courses in cyber security domain.
- Strengthen cyber deterrence:
- According to the International Institute for Strategic Studies (IISS), India is positioned among the third-tier countries on a spectrum of cyber warfare capabilities.
- Given the increasing risk of ransomware attacks, confrontations with China and threats from non-state actors, India needs to harness its digital-industrial potential and adopt a whole-of-society approach to improve its cyber security.
- International cooperation:
- Global tie-ups should be ensured in creating a peaceful cyber space.
- There should be enhanced cooperation among nations, reaffirming a global call to action for all United Nations member nations to not attack the core of the Internet even when in a state of war
- Focussing cyber safety of children:
- Creating a child-safe digital spaces >> essential for online education, digital awareness and creating digitally empowered future generation.
- Upgrade Cyber cells:
- The existing cyber cells needs upgradation by setting up dark web monitoring cells and social media monitoring cells, induct technical experts, along with traditional police recruitments.
- Address gender gap in cybersecurity workforce:
- The global cybersecurity workforce was woefully lacking in gender diversity.
- Leaving women out of the cybersecurity workforce leaves talent on the table and will only hurt these countries’ ability to close the skills gap
- To address shortage of 3.5 mn security professionals globally by 2025, we need to promote more women workers in the sector.
CASE STUDY: KERALA’S CYBERDOME PROJECT
- Cyberdome is the Kerala Police Department’s premier facility dedicated to prevent cybercrime and mitigate cybersecurity threats to the State’s critical information infrastructure.
- It involves a team of ethical hackers, expert coders, youth prodigies skilled in software, law enforcers and civilian volunteers.
- It is envisaged as a collaboration Centre for both the public and private fraternity to converge and share information, as well as resources,that will escalate the safety of our cyber space.
- It has also used social engineering as the lynchpin of its policing strategy to snoop on radical groups that use the net for extremist activities.
- In March 2017, Cyberdome notched up a remarkable victory when it forewarned the Kerala government of a possible ransomware attack.
- Cyberdome has developed cyber-surveillance tools to detect and convict those responsible for industrial espionage.
- Cyberdome has also partnered with the Interpol and the International Centre for Missing and Exploited Children (ICMC) to combat child porn.
PRACTICE QUESTION:
Q. Examine the evolution of cybersecurity threats in the post-pandemic world?


