India and Cyber security
2021 JUL 5
Mains >
Security > Cyber Security > Cyber warfare
IN NEWS:
- India has made it to the top 10 in Global Cybersecurity Index (GCI) 2020 by International Telecommunication Union, moving up 37 places from the previous ranking.
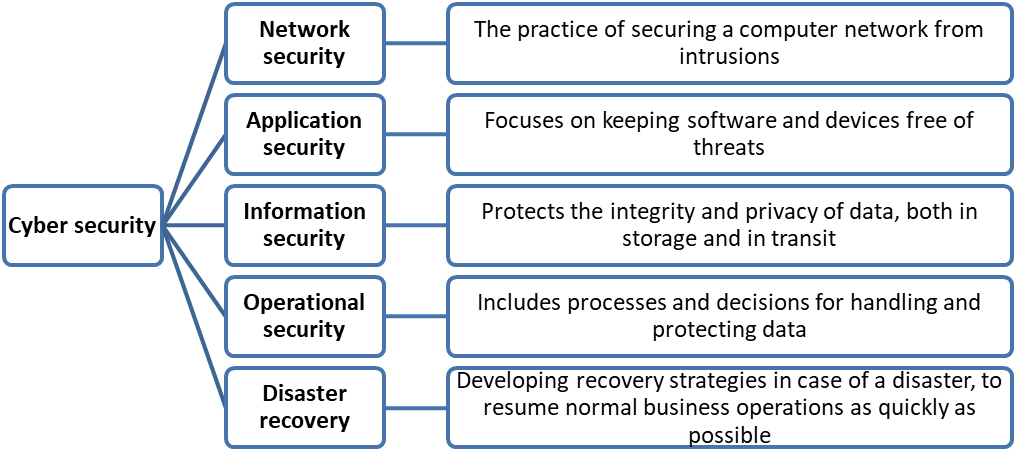
CYBER SECURITY:
- Cyber security involves the techniques of protecting computers, networks, programs and data from unauthorized access or attacks that are aimed for exploitation.
- The concept includes guidelines, policies, safeguards, technologies, tools and training to provide the best protection for the cyber environment and its users.
CYBERATTACK:
- Cyberattack can be defined as any act that compromises the security expectations of an individual, organization, or nation in its cyber space.
TYPES OF CYBER ATTACKS:
Based on perpetrators and their motives, Cyber threats can be categorized into:
- Cyber Espionage:
- Refers to the use of computer networks to gain illicit access to confidential information, typically that held by a government or other organization.
- The 2019 cyber-attack on Kudankulam nuclear power plant using a data extraction malware falls under this category.
- Cyber Crime:
- Cybercrime is any criminal activity that involves a computer, networked device or a network.
- Most cybercrimes are carried out in order to generate profit for the cybercriminals. However, some cybercrimes are carried out against computers or devices directly to damage or disable them, to spread malware, illegal information, images or other materials. Some cybercrimes do both.
- Cyber Terrorism:
- It is the convergence of terrorism and cyber space. It refers to unlawful attacks and threats of attacks against computers, networks and information stored to intimidate or coerce a government or its people in furtherance of political or social objectives.
- They are offensive maneuvers that targets computer information systems, infrastructures or computer networks, with an intention to damage or destroy targeted computer network or system.
- Cyber Warfare:
- Though there is no proper definition, it may be defined as actions by a nation-state or its proxies to penetrate another nation’s computers or networks for the purposes of espionage, causing damage or disruption.
- It is perceived to be the fifth domain of warfare.
TYPES OF CYBERCRIMES:
- Hacking: It is the unauthorized accessing of a computer device or a computer network. Those who engage in the activity are called hackers.
- Cyber stalking: It is the use of various online platforms as well as other electronic devices to stalk, harass, or blackmail any person or group.
- Online identity theft: This is when a person steals another person’s information (Social Security number, credit card information, bank account numbers etc) through online means. It can be achieved in a variety of ways such as email phishing, malware injection, and brute force hacking.
- Online child abuse: There are many activities that constitute online child abuse including the downloading, selling, and distribution of child pornography through websites and forums and the solicitation of children for sex via chat rooms.
- Ransomware attack: A ransomware attack is when a cybercriminal injects a specific kind of malware (called ransomware) into your device. The ransomware is designed to block access to your data until a certain amount is paid, thereby holding it for ransom. In most cases, ransoms are demanded to be paid in bitcoins or other cryptocurrencies.
- Internet fraud (online scams): The purpose of an online scam is for you the victim, into willingly giving up money under false pretenses.
|
Cyberspace related terms
|
|
Malware
|
- Any “malicious software” designed to secretly access your computer.
Types:
- Virus: A type of malware aimed to corrupt, erase or modify information on a computer before spreading to others.
- Trojan Horse: A piece of malware that often allows a hacker to gain remote access to a computer through a “back door”. Eg: Eventbot malware
- Worm: A piece of malware that can replicate itself in order to spread the infection to other connected computers.
|
|
Distributed Denial of Services (DDoS)
|
- A form of cyber attack which aims to make a service unusable by “flooding” it with malicious traffic or data from multiple sources.
- One of the recently discovered DDoS malware was ‘Saposhi’
|
|
Bot & Botnet
|
- A type of software application or script that performs tasks on command, allowing an attacker to take complete control remotely of an affected computer.
- A collection of these infected computers is known as a “botnet” and is controlled by the hacker or “bot-herder”
|
|
Phishing
|
- It is an email sent from an internet criminal disguised as an email from a legitimate, trustworthy source. The message is meant to lure you into revealing sensitive or confidential information.
- Its advanced form is spear phishing.It occurs when criminals obtain information about you from websites or social networking sites, and customize a phishing scheme to you.
|
|
Spamming
|
- It is unsolicited email, instant messages, or social media messages. These messages are fairly easy to spot and can be damaging if you open or respond.
|
|
Spoofing
|
- Criminal activity where a criminal impersonates another individual or organization, with the intent to gather personal or business information.
|
|
Pharming
|
- It is the use of a malicious website that resembles a legitimate website, used to gather usernames and passwords.
|
|
Hacktivism
|
- Hacking for politically or ideologically motivated reasons
|
INDIA & CYBERCRIMES:
- As per the Indian Computer Emergency Response Team (CERT-In) data, nearly 1.16 million cases of cyberattacks were reported in 2020, up nearly three times from 2019 and more than 20 times compared to 2016.
- The NCRB's 2019 crime data showed a 60.4 percent increase in number of cases registered in 2019 as compared to 2018.
- As per the IBM analysis, India was the second-most targeted country in the Asia-Pacific region in 2020 as far as cybercrimes are concerned, with a 7 % share in such incidents globally.
- Ransomware was the most rampant cybercrime accounting for 40% of all attacks.
- Finance and insurance were the most targeted sector in India (60 per cent), followed by manufacturing and professional services.
- Cases of serious cyber-attacks have been on the rise in India. Some of these include:
- Attack on Air India (2021): India's national airline suffered a cyber-attack on its data servers, which affected about 4.5 million customers around the world. Details including passport and ticket information as well as credit-card data were compromised.
- Data breach on Domino’s India (2021): Jubilant FoodWorks, which owns Domino's India, experienced a security incident where data of 18 crore orders of Domino's India became public.
- Malware attack at Kudankulam Nuclear Power Plant (2019): A malware infection was detected on the administrative network used for day-to-day administrative activities.
- Aadhaar data leak (2019): As recently as February 2019, Aadhaar details of over 6.7 Mn users containing details such as names, addresses and the numbers were leaked.
- Cyber Attack on Cosmos Bank (2018): A cyber-attack on Cosmos Bank’s Pune branch saw nearly 94 crores rupees being siphoned off by hackers to a Hong Kong situated bank.
- WannaCry & Petya ransomware attacks (2017): The ransomware attacks made its impact felt across the world, including India, where several thousand computers got locked down by ransom-seeking hackers. The attack also impacted systems belonging to the Andhra Pradesh police and state utilities of West Bengal and certain functions at Jawaharlal Nehru Port Trust.
- Data thefts at Zomato (2017): The food tech company discovered that data, including names, email IDs and hashed passwords, of 17 million users was stolen by a hacker.
THREATS TO INDIA’S CYBER SECURITY:
- Large share of internet users & Digital illiteracy:
- India is home to the 3rd largest population of internet users. By 2020, India has around 730 million internet users, with 75% of new users from rural areas.
- However large shares of these users are digitally illiterate. According to a recent report by the Digital Empowerment Foundation, digital literacy is almost no-existent among more than 90% of India’s population.
- Exponential growth of digital space:
-
- The pandemic has resulted in digital technology adoption being fast forwarded and the demand for technology-driven products increasing multifold. But this growth has further exposed our cyber vulnerabilities.
- Eg: Since 2020, cyber criminals are increasingly using relief efforts and public health information as spam lures, including targeted attacks on critical components of the vaccine supply chain.
- Also, children have become more prone to online bullying, given the longer hours spent over the internet due to online classes.
- Service hub:
- India is home to a large share of IT and service-sector industries. It hosts some of the largest outsourcing services in the world.
- To add to this, through several initiatives such as Digital India, the government is pushing for large scale digitization. This not only attracts tech investors, but also tech criminals.
- Obsolete systems:
- India is a major destination for cheap electronic imports with inadequate security features. Also, there is rampant use of unlicensed software and cracked licenses. These factors make the country susceptible to hacking and other malware attacks.
- Import dependency:
- Most equipment and technology for setting up Cyber Security infrastructure in India are currently procured from global sources. These systems are vulnerable to cyber threats just like any other connected system.
- These risks can be in the form of inclusion of faults or backdoors in the system, insertion of hidden methods, Hardware tampering etc.
- Offshore servers:
- Most service providers in India use data servers and processing centers located beyond the geographical boundary of India.
- This has proved to be a major hindrance in investigating cybercrimes and ensuring that the firms abide by the Indian cyber and privacy laws.
- Under reporting:
- As per National Crime Records Bureau, Cybercrimes accounted for less than a percentage (0.43%) or 21,796 cases of a total of 50,07,044 cognizable crimes in 2017. This indicates a severe case of under reporting of cybercrimes.
- A major reason for the same among individuals is the lack of awareness regarding cybersecurity. In case of organisations and Service sector industries, it is the fear of loss of reputation.
- Shortage of professionals:
- Despite having high demand for cybersecurity professional, India is facing an acute talent shortage in this sector. It has been estimated that as of 2020-end, India faced a shortage of 1.5 million cyber security professionals.
- Jurisdictional Uncertainty:
- Cybercrimes cut across territorial borders which undermine the feasibility and legitimacy of applying domestic laws. In the absence of a single internationally recognized code of law and procedure governing cybercrimes the law enforcing authorities of individual countries find it extremely difficult to tackle cybercrimes and criminals while applying their territorial law.
- Limited inter-agency coordination:
- Cyber crimes often pans across the jurisdiction of different agencies, such as state police forces, Enforcement Directorate, departments under Home and Foreign Affairs Ministries etc.
- However, till recently there has been no proper mechanism to ensure the smooth coordination between these agencies in matters of data sharing, investigation etc.
- Private sector, despite being a major stakeholder in the cyberspace, has not been involved proactively for the security of the same.
INDIA’S APPROACH TO CYBER SECURITY:
I. LEGISLATIVE MEASURES:
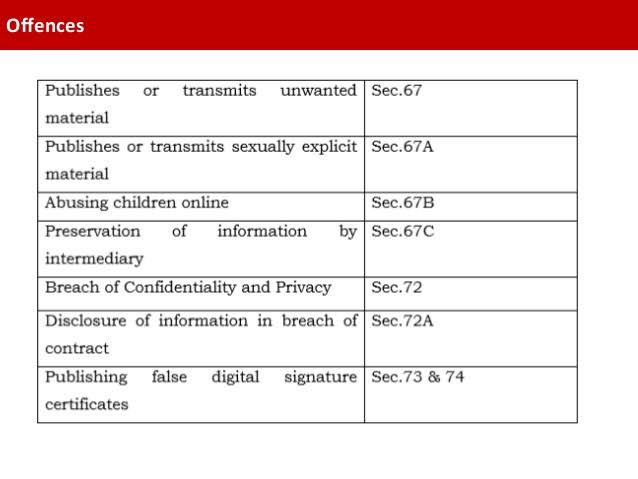
- Information Technology Act, 2000:
- It includes provisions dealing with unauthorized use of internet or computers. It is often referred to as the cyber law of India.
- It contains a wide range of offences such as tempering with computer sources, sending offensive messages, violation of privacy; publishing obscene material etc., all of which are recognized as illegal activities under the Indian Penal Code.
-
- Provides for the establishment of a Cyber Regulatory Appellant Tribunal under the Act. This tribunal will handle all appeals made against the order of the Controller or Adjudicating Officer.
- In 2008, the Act was amended to remove the controversial Section 66A which dealt with actions against offensive contents on websites.
- National Cyber security Policy 2013:
- The Policy document outlines a roadmap to create a framework for comprehensive, collaborative and collective response to deal with the issue of cyber security at all levels within the country.
- Salient features:
- Goals aimed at reducing national vulnerability to cyber attacks, preventing cyber attacks & cyber crimes, minimising response & recovery time and effective cybercrime investigation and prosecution.
- Focused actions at the protection of critical information infrastructure and national alerts and advice mechanism, awareness & capacity building and promoting information sharing and cooperation.
- Enhancing cooperation and coordination among all the stakeholder entities within the country.
- Framework and initiatives that can be pursued at the Govt. level, sectoral levels as well as in public-private partnership mode.
- Facilitates monitoring of key trends at the national level such as trends in cyber security compliance, cyber attacks, cyber crime and cyber infrastructure growth.
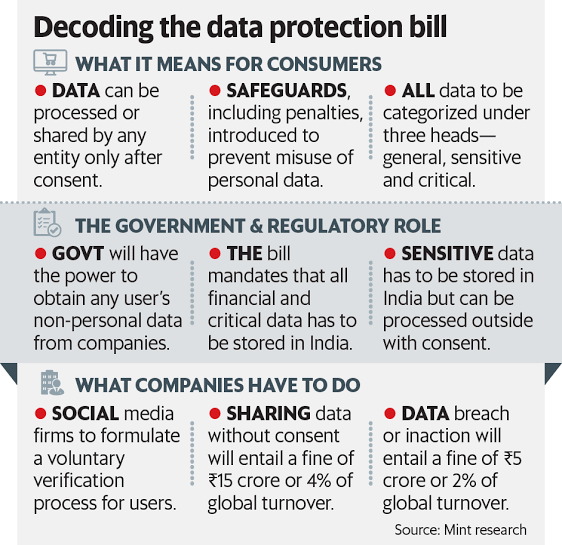
- Personal Data Protection Bill, 2019:
- The Bill seeks to provide for protection of personal data of individuals, and establishes a Data Protection Authority for the same.
- The Bill categorizes data into three: Personal data, Sensitive personal data and Critical personal data.
- The Bill gives the government powers to authorise the transfer of certain types of personal data overseas and has given exceptions allowing government agencies to collect personal data of citizens.
- It also mandates data fiduciaries to provide the government with any non-personal data when demanded.
- Cyber Security Strategy:
- The government is expected to release a new cybersecurity strategy this year. The vision of this strategy is to ensure safe, secure, resilient, vibrant, and trusted cyber space.
II. INSTITUTIONAL MEASURES:
- Indian Computer Emergency Response Team (CERT-in):
- It is an office within the Ministry of Electronics and Information Technology that deals with cyber security threat.
- Its mandate is to protect Indian cyberspace and software infrastructure against destructive and hacking activities. It also responds to computer security incidents, report on vulnerabilities and promote effective IT security practices throughout country.
- National Information Centre-Computer Emergency Response Team (NIC-CERT):
- A setup of National Informatics Centre (NIC) to prevent and predict cyber-attacks on government utilities.
- It will monitor and help in early detection and mitigation of cyber attacks on government networks.
- National Critical Information Infrastructure Protection Centre (NCIIPC):
- It is an organisation of created under the Information Technology Act, 2000 to battle cyber security threats in strategic areas such as air control, nuclear and space.
- It will function under the National Technical Research Organisation, a technical intelligence gathering agency controlled directly by the National Security Adviser in PMO.
- National cyber coordination centre (NCCC):
- It is a cybersecurity and e-surveillance agency that scans communication metadata and provides real time situational awareness and alert various security agencies.
- Cyber and Information Security (CIS) Division:
- It has been created under the Ministry of Home Affairs to tackle internet crimes such as cyber threats, child pornography and online stalking.
- Under this, Indian cybercrime coordination centre (I4C) and Cyber Warrior Police force has also been established.
- Cyber Surakshit Bharat:
- It is first public-private partnership of its kind and will leverage the expertise of the IT industry in cybersecurity and aims at awareness generation & capacity building.
- It includes awareness programs on the importance of cybersecurity, series of workshops on best practices and enablement of officials with cybersecurity health tool kits to manage and mitigate cyber threats.
- Cyber Swachhta Kendra:
- It is the Botnet Cleaning and Malware Analysis Centre under the Ministry of Electronics and Information Technology (MeitY) to create a secure cyber space by detecting botnet infections in India, enable cleaning and secure systems so as to prevent further infections.
- Defence Cyber Agency:
- It is a proposed tri-service agency that seeks to strengthen India’s cyber warfare capabilities.
- It will work in conjunction with the National Cyber Security Advisor and would include as many as 1000 personnel from all three branches, the Army, Navy and the Air force.
III. INTERNATIONAL COLLABORATIONS:
- India-Australia Collaboration for Cyber Technology:
- In June 2021, India and Australia signed a four-year collaboration on cyber affairs and critical technologies.
- Both the parties agreed to work hand-in-hand to promote and preserve an open, free, safe and secure internet, enhance digital trade, harness critical technology opportunities, and address cybersecurity challenges.
- Research and development in various technologies such as artificial intelligence, quantum computing, and robotics will also be carried out.
- Discussions in the UN:
- India has been utilizing the UN to raise its concerns on increasing cyber attacks.
- Eg: In June 2021, India raised concerns about cross-border state-sponsored cyber-attacks during the UNSC Open Debate on "Maintenance of International Peace and Security: Cyber Security".
OTHER GLOBAL INITIATIVES:
- The International Telecommunication Union (ITU):
- It is a specialized agency within the UN which plays a leading role in the standardization and development of telecommunications and cyber security issues.
- Budapest Convention on Cybercrime:
- It is an international treaty that seeks to address Internet and computer crime by harmonizing national laws, improving investigative techniques, and increasing cooperation among nations.
- India is not a signatory to this convention.
- Global Centre for Cybersecurity:
- It was launched by the World Economic Forum (WEF) to serve as laboratory and early-warning think tank for future cyber security scenarios and help build a secure global cyberspace.
- Internet Governance Forum (IGF):
- It brings together all stakeholders i.e. government, private sector and civil society on the Internet governance debate. It was first convened in October–November 2006.
- Internet Corporation for Assigned Names and Numbers (ICANN):
- It is a non-profit organization responsible for coordinating the maintenance and procedures of several databases related to the namespaces and numerical spaces of the Internet, ensuring the network's stable and secure operation. It has its headquarters in Los Angeles, U.S.A.
WAY FORWARD:
India is expected to be one of the largest players in the cyberspace in the coming years. But for it to be safe and beneficial, India needs to ensure a proper regulatory environment that ensures privacy and fair play.
- Create an all-encompassing policy: Presently, there are no acceptable norms of behavior in cyberspace. Cyberspace is a rapidly evolving area and hence, India needs to update its policy on cybersecurity.
- Human resource development: By 2025, the cybersecurity space is expected to generate around a million jobs in India. For it to be beneficial for India’s demographic dividend, India must invest in capacity building and skill development.
- Thrust on digital literacy: Digital literacy must be made part and parcel of school curriculums. People must be made aware of the relevance of cyber security. For the same, the scope of initiatives under Digital India campaign needs to be enlarged.
- ‘Atmanirbhar’ in cyber systems: Indigenous capability in manufacture of electronics should be boosted, so as to reduce India’s import dependency. The government should also strengthen its monitoring of electronics import, so that only reliable products make their way to the Indian markets.
- Zero-trust approach: Zero trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network. Organizations need to adopt a zero-trust approach to their security strategy.
- Promote cutting edge technologies: Research should be encouraged to leverage artificial intelligence (AI) to monitor, detect and verify the legitimacy of threats and automate response to the threats.
- Encourage investment in cybersecurity: The private must be persuaded to actively invest in cyber security. At present, only a part of security budget is being utilized for IT security by companies. The government should can also play its role, by creating degree and PG courses in cyber security domain.
- Strengthen cyber deterrence: According to the International Institute for Strategic Studies (IISS), India is positioned among the third-tier countries on a spectrum of cyber warfare capabilities. Given the increasing risk of ransomware attacks, confrontations with China and threats from non-state actors, India needs to harness its digital-industrial potential and adopt a whole-of-society approach to improve its cyber security.
- International cooperation: Global tie-ups should be ensured in creating a peaceful cyber space. There should be enhanced cooperation among nations, reaffirming a global call to action for all United Nations member nations to not attack the core of the Internet even when in a state of war.
|
CASE STUDY: Kerala’s Cyberdome project
- Cyberdome is the Kerala Police Department’s premier facility dedicated to prevent cybercrime and mitigate cybersecurity threats to the State’s critical information infrastructure.
- It involves a team of ethical hackers, expert coders, youth prodigies skilled in software, law enforcers and civilian volunteers.
- It is envisaged as a collaboration Centre for both the public and private fraternity to converge and share information, as well as resources, that will escalate the safety of our cyber space.
- It has also used social engineering as the lynchpin of its policing strategy to snoop on radical groups that use the net for extremist activities.
- In March 2017, Cyberdome notched up a remarkable victory when it forewarned the Kerala government of a possible ransomware attack.
- Cyberdome has developed cyber-surveillance tools to detect and convict those responsible for industrial espionage.
- Cyberdome has also partnered with the Interpol and the International Centre for Missing and Exploited Children (ICMC) to combat child porn.
|
PRACTICE QUESTION:
Q. Examine the causes of rising cybercrimes in India. What measures have the government taken to enhance India’s cybersecurity?



